Online payment fraud losses are expected to exceed $25 billion annually by 2024, and honestly? That number hit me like a brick when I was going through my own company’s security stuff last month. I found three sketchy transactions on our business account – thank god our bank caught them – but it made me realize just how exposed we all are out here in the digital wild west.
Every single day, thousands of businesses get hit by scams that are getting scarier and more sophisticated. We’re not just talking about the money that gets stolen – though that’s bad enough. It’s the reputation damage, the customers who’ll never trust you again, the regulatory fines, and all those hidden costs when you’re scrambling to figure out what the hell happened.
What really freaks me out is how these fraudsters have evolved. We’re not dealing with some kid in his mom’s basement trying to use stolen credit cards anymore. These are full-blown criminal operations that could fool security professionals who’ve been doing this for decades.
If you’re running any kind of online business, you need to understand these patterns – especially when you’re thinking about e-commerce marketing strategies that balance keeping customers happy while actually protecting them.
I’ve put together 25 real-world cases that’ll show you exactly how bad it can get out there. These aren’t just numbers on a spreadsheet – they’re cautionary tales that reveal how these criminals think and what you can actually do to protect yourself. Each case study shows just how creative and patient these scammers have become.
Table of Contents
- Payment and Credit Card Fraud Cases
- Identity Theft and Account Fraud Cases
- Merchant and Seller Fraud Cases
- Supply Chain and Logistics Fraud Cases
- Technology and Platform Exploitation Cases
- Social Engineering and Phishing Cases
- Key Analysis and Prevention Strategies
- How The Marketing Agency Can Help
TL;DR
- Synthetic identity fraud is the scariest thing I’ve researched – criminals spend 18+ months building fake people before they strike
- Account takeover attacks exploded 347% during the pandemic, with businesses losing an average of $12,000 per hit
- Fake online stores can look so professional they fool thousands of customers while stealing millions
- Insider threats in shipping and warehouses are way more common than you’d think
- Your mobile apps and APIs might be leaking customer data right now without you knowing it
- Social engineering attacks work because they target the one security flaw you can’t patch – human nature
- The good news? Most of this stuff is preventable if you know what to look for
- The best protection combines smart technology with proper training – you need both
Payment and Credit Card Fraud Cases
Payment fraud is where criminals hit you hardest in the wallet. These schemes range from incredibly sophisticated identity creation to automated attacks that test thousands of credit cards per hour. What’s scary is how they exploit both technology gaps and human psychology to steal millions.
| Fraud Type | Average Loss Per Hit | How Long Until You Notice | How Hard to Stop |
|---|---|---|---|
| Fake Identity Fraud | $4,600 | 18+ months | Nearly impossible |
| Account Takeover | $12,000 | 2-7 days | Doable with right tools |
| Card Testing | $3.75 per test | Hours to days | Pretty easy actually |
| Email Scams | $180,000 | 1-4 weeks | Really tough |
| Triangulation Fraud | $850 per incident | 30-90 days | Medium difficulty |
1. Synthetic Identity Payment Fraud
Okay, this one honestly blew my mind when I first dug into it. These criminal organizations spent 18 months – a year and a half! – building over 500 completely fake people using bits of real Social Security numbers mixed with made-up names and addresses. They weren’t rushing anything. They played the long game, slowly building credit histories by becoming authorized users on real accounts and applying for small credit lines.
Here’s the scary part – these fake identities ended up with credit scores above 650. That means they looked completely legit to every fraud detection system out there. Then, during Black Friday weekend, they struck like lightning across 50+ retailers and walked away with $2.3 million.
What makes this absolutely terrifying is that traditional fraud systems completely missed it. These “people” had established credit histories and normal shopping patterns. The scammers used reshipping services and money mules to get the goods, creating layers upon layers that made it nearly impossible for law enforcement to trace.
Picture this: a criminal creates “John Martinez” using a real Social Security number from someone who died, adds a fake address that actually exists, and spends 18 months building his credit. They make him an authorized user on existing accounts, get him small credit cards, and make regular payments. By Black Friday, “John Martinez” has a 680 credit score and successfully buys $15,000 worth of electronics from multiple stores before vanishing into thin air.
2. Account Takeover via Credential Stuffing
These cybercriminals had bots running 24/7, trying 50 million stolen username and password combinations against a major fashion retailer’s login system. Think about that for a second – 50 million attempts. It’s like having a robot try every key in the city until it finds ones that open your front door.
The numbers are staggering: they cracked 75,000 customer accounts in just a few days. Once they were in, they went on a shopping spree using stored payment methods and loyalty points, racking up $890,000 in fraudulent purchases.
The really frustrating part? Many of these accounts had been sitting dormant for months, so customers didn’t even notice the unauthorized activity right away. The attack worked because people reuse the same password everywhere – when some other company gets hacked, those passwords become weapons against completely different businesses.
3. Card Testing Attacks
Picture fraudsters with a massive list of stolen credit card numbers, but they don’t know which ones still work. So they built a system to make thousands of tiny test purchases – $1 to $5 – on an electronics retailer’s website. They weren’t trying to get rich quick; they were quality-testing their stolen goods before selling verified card numbers on the dark web.
The retailer got hit with 12,000 test transactions totaling $45,000 in direct losses. But here’s the kicker – the real damage came from $230,000 in chargeback fees and processing costs. Each tiny transaction created administrative overhead that cost way more than the actual purchase amount.
This type of scam is particularly nasty because those small amounts often go unnoticed on credit card statements for weeks or months. By the time cardholders figure it out, criminals have already sold the “verified good” card numbers to other scammers.
4. Business Email Compromise (BEC) in B2B E-Commerce
These scammers are basically evil psychologists. They spent months researching a B2B industrial equipment supplier, stalking executives on LinkedIn and Facebook, learning the company hierarchy and who talks to whom. They knew exactly which buttons to push.
Then they hacked the CFO’s email through a perfectly crafted phishing attack and started sending “urgent” payment requests to the accounts payable team. The emails looked completely legitimate because they were coming from the actual CFO’s account, asking for wire transfers to pay “time-sensitive” supplier invoices.
When I saw that $1.8 million number, my stomach dropped. That’s not just money – that’s potentially someone’s entire business going under because they trusted the wrong email. The psychological manipulation was expertly crafted, creating artificial panic while leveraging the authority of a senior executive.
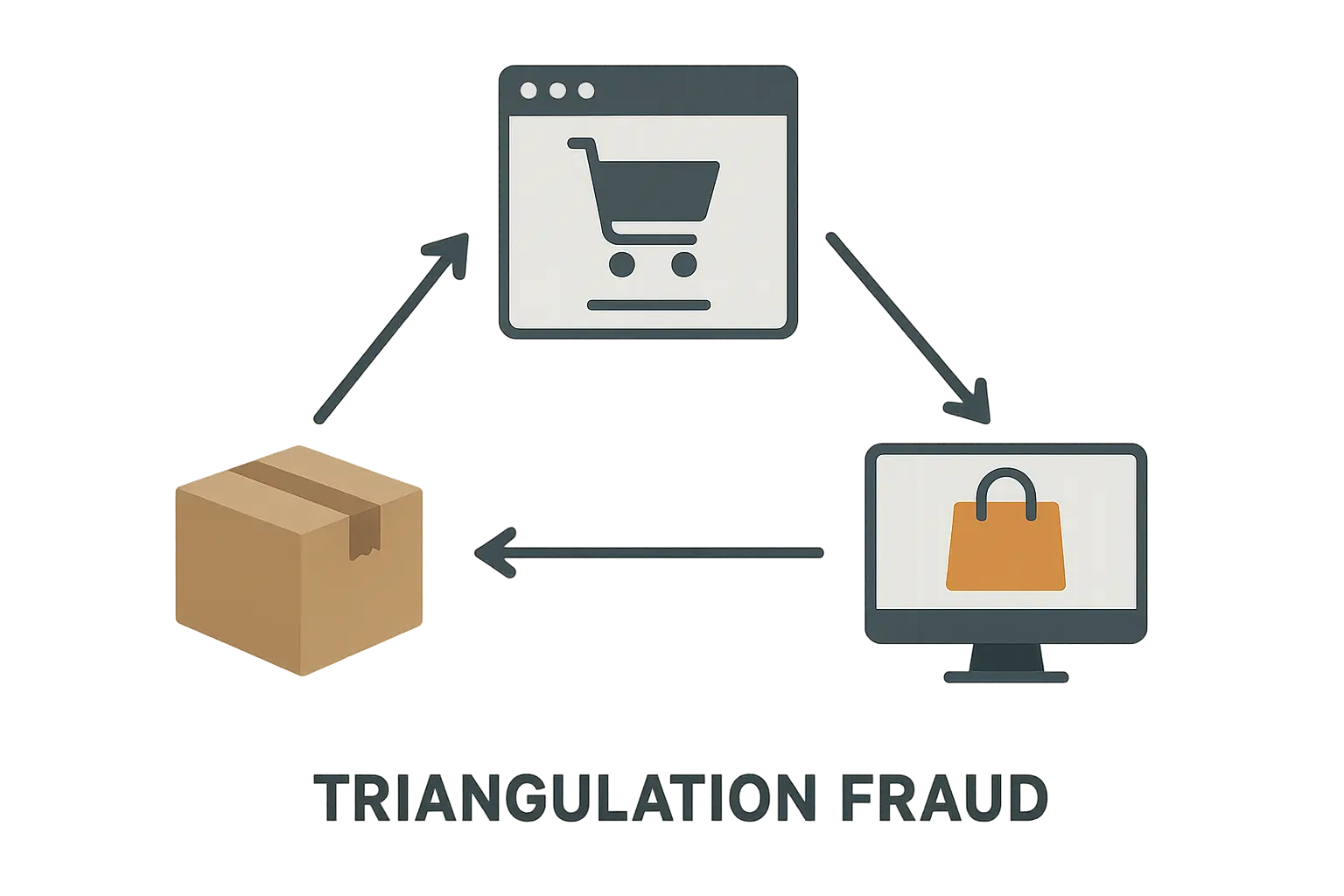
5. Triangulation Fraud in Marketplace Settings
Think of this like a shell game, but instead of three cups, there are dozens of players all getting screwed in different ways. Fraudsters created fake seller accounts on major marketplaces, collected payments for products they promised to deliver, then used stolen credit cards to buy those same items from legitimate retailers and ship them directly to the buyers.
Here’s the genius (and I hate that I’m calling it genius): buyers actually got their products as promised, legitimate sellers made sales, and nobody immediately realized anything was wrong. The stolen credit card holders only discovered the unauthorized charges weeks later, giving the scammers plenty of time to disappear.
This scam exploits the trust that makes marketplaces work while spreading the financial damage across multiple victims. It’s like a criminal version of three-card monte, except everyone loses.
6. Refund Fraud Through Return Policy Exploitation
Organized groups figured out how to game a luxury retailer’s generous return policy by buying expensive items, returning cheap knockoffs or damaged junk, and reselling the original products. They weren’t amateurs – they studied the return process like it was their job.
Over 8 months, they stole $340,000 before pattern recognition finally caught them. These criminals understood exactly how the retailer processed returns and found every gap in their verification procedures. They used different return locations and timed everything perfectly to avoid triggering automated fraud detection.
What made this so effective was the calculated approach – they knew that most retailers don’t have the time or resources to carefully inspect every return, especially during busy periods.
Identity Theft and Account Fraud Cases
Identity theft has gone way beyond simple credit card fraud. We’re talking about sophisticated operations that target medical records, steal from children who haven’t even learned to drive yet, and prey on vulnerable populations. These cases show how personal information has become a commodity in criminal enterprises that can stay hidden for years.
7. Medical Identity Theft in Health E-Commerce
This one really gets to me. Fraudsters got their hands on medical records from a healthcare data breach and weaponized patient information to create fake accounts on prescription delivery platforms and medical supply websites. They had everything – insurance details, medical history, prescription information.
They created accounts using real patient identities but changed the contact info to their own addresses, then ordered expensive medical equipment and prescription medications. The patients’ insurance covered the costs while criminals redirected everything to addresses they controlled.
The financial hit reached $1.2 million across multiple healthcare platforms. But imagine finding out you can’t get the insulin you need because some criminal already “bought” it using your identity. People could literally die from this stuff. The long-term damage to patients was devastating – insurance claim denials for legitimate medical needs, trashed credit scores, and compromised medical histories.
8. Child Identity Theft for Clean Credit Profiles
Can we talk about how messed up this is for a second? A criminal network systematically harvested kids’ personal information from school databases and social media to create fraudulent accounts with squeaky-clean credit profiles. The worst part? The fraud stayed hidden for an average of 7 years until these kids applied for their first credit cards or student loans.
The damage reached $3.4 million across 1,200 stolen identities. Children’s identities are gold to criminals because they offer years of undetected use before anyone figures it out. These kids could be 25 years old before they realize their credit was destroyed when they were 8.
Picture this: a 16-year-old applies for their first part-time job and discovers $45,000 in fraudulent accounts opened over three years – credit cards, auto loans, retail financing, the works. The family ends up spending 18 months and $3,000 in legal fees just to restore their teenager’s credit before college applications.
9. Elderly Targeting Through Social Engineering
My heart breaks for these folks. Phone scammers convinced elderly victims to hand over personal information by pretending to be from their bank doing “account security verification.” These people grew up in a world where a handshake meant something, and now faceless criminals are preying on basic human decency.
The average loss per victim was $2,400 across 300 confirmed cases. The criminals specifically targeted elderly people because they’re more likely to trust authority figures and less familiar with common scam tactics. The emotional manipulation was particularly cruel – threats about account closures or security breaches designed to create panic.
Recovery was complicated because many victims were embarrassed about being deceived and waited too long to report the fraud. Nobody wants to admit they got conned, especially when family members might start questioning their ability to handle their own finances.
10. Government Benefits Identity Fraud
Fraudsters used stolen information from government benefit recipients to create accounts and buy gift cards, basically converting food stamps and assistance money into cash they could pocket. The scheme generated $560,000 in fraudulent purchases using compromised EBT and government assistance accounts.
The criminals targeted vulnerable populations who were less likely to have sophisticated fraud monitoring and might not immediately notice unauthorized activity. This type of fraud hits people who are already struggling, creating additional hardship for families that depend on government assistance.
It’s not just about the money – it’s about stealing from people who literally can’t afford to lose anything.
11. Social Media Identity Harvesting
And here’s something that’ll make you paranoid – automated bots were probably scrolling through your Facebook and Instagram right now, taking notes on your dog’s name, your favorite restaurant, and where you work. They scraped personal information from 2,000 social media profiles to create fake accounts on e-commerce platforms.
The scary part isn’t just the automation – these bots could process thousands of profiles daily, faster than you could scroll through your own feed. They extracted names, addresses, phone numbers, and all those personal details people freely share online without thinking twice.
Many victims had no idea their social media info was being harvested until they got notifications about accounts they never created. The operation resulted in $180,000 in unauthorized purchases using publicly available information that people voluntarily posted.
Merchant and Seller Fraud Cases
Now we’re getting into cases where criminals create entire fake businesses or exploit legitimate platforms to rip off consumers and other businesses. These operations can look so professional they fool thousands of customers while stealing millions of dollars.
12. Phantom Merchant Scheme
This operation created completely fake online businesses with professional websites, actual customer service departments, and marketing campaigns that would make legitimate companies jealous – all to collect payments for products they never intended to deliver. The level of sophistication was honestly impressive in the most terrifying way possible.
These criminals didn’t just throw up a quick website and hope for the best. They established businesses with proper licensing and registration, created professional websites with fake customer testimonials and detailed product catal ogs, hired people to run customer service operations, and maintained credibility for 6-8 weeks before disappearing with everyone’s money.
They’d rinse and repeat with new business identities and domain names. Over 12 phantom businesses, they collected $4.2 million from 8,000 customers. That’s over 500 bucks stolen from each person – enough to ruin someone’s Christmas or force them to skip paying bills.
The professional marketing campaigns, SEO optimization, and social media presence made these businesses appear completely legitimate. They even employed sophisticated SEO strategies to rank highly in search results, making their scams look more credible to unsuspecting customers.
13. Dropshipping Counterfeit Goods
A network of sellers used major e-commerce platforms to sell fake luxury goods sourced from overseas manufacturers. They used dropshipping to avoid getting caught with inventory, selling 15,000 counterfeit items across 200 seller accounts over 18 months.
The operation generated $2.8 million in sales of fake merchandise while causing serious brand damage to legitimate manufacturers. The dropshipping model made it almost impossible for platforms to detect the counterfeit products until customers started complaining.
These criminals were like digital cockroaches – as soon as one seller account got shut down, three more would pop up. They maintained a constant presence on major platforms by constantly creating new identities.
14. Fake Review Manipulation Networks
Organized groups created thousands of fake customer accounts to manipulate product reviews and seller ratings, artificially boosting crappy or fraudulent products in search rankings. We’re talking about 50,000 fake reviewer accounts posting over 200,000 fraudulent reviews across multiple platforms.
Legitimate businesses saw their sales drop by 40% on average because fake competitors were artificially inflated in the rankings. The manipulation was sophisticated enough to fool automated systems designed to spot fake reviews.
I’ve been in marketing for years, and even I almost fell for one of these fake review schemes. If it can fool me, it can fool anyone. The economic impact went way beyond individual businesses – it undermined consumer trust in online review systems entirely.
15. Subscription Box Fraud
A fraudulent subscription service collected monthly payments for “curated product boxes” while delivering cheap junk worth only 10-15% of what customers were paying. They marketed premium experiences while providing dollar store garbage.
The operation collected $890,000 from 3,200 subscribers before getting shut down. The criminals maintained the facade through professional marketing and carefully managed customer service designed to delay complaints and cancellations for as long as possible.
Many subscribers kept paying for months before realizing they were getting ripped off. The disparity between what was promised and what actually showed up in those boxes was just insulting.
16. Affiliate Marketing Click Fraud
Sophisticated bot networks generated fake traffic and conversions for affiliate marketing programs, stealing commissions from legitimate affiliates while inflating merchant advertising costs. The technical setup included residential proxy networks to make the fake traffic look like real people browsing and buying.
The criminals created entire fake customer journeys with realistic browsing patterns, generated fraudulent conversions using stolen payment information, and even used machine learning to adapt when fraud detection systems tried to catch them. The operation generated $1.6 million in fraudulent affiliate commissions over 12 months.
The impact went beyond just stolen money – it made affiliate marketing less effective as a customer acquisition channel because merchants couldn’t trust their data anymore.
Supply Chain and Logistics Fraud Cases
Supply chain fraud exploits the physical movement of goods and how complex shipping networks have become. These schemes often involve inside jobs and can result in massive losses while being incredibly hard to detect because everything is spread out across different warehouses and delivery routes.
17. Package Interception Networks
A criminal organization infiltrated shipping and logistics networks to systematically steal high-value packages during transit. They recruited delivery drivers and warehouse workers as inside collaborators, creating a network that spanned 15 major cities.
The operation was like something out of a heist movie – they identified valuable packages through shipping manifests and tracking systems, redirected packages to addresses they controlled, and resold stolen merchandise through secondary e-commerce channels. They were smart enough to avoid packages with GPS monitoring.
The financial damage reached $3.1 million across 12,000 intercepted packages. The geographic coordination required serious organizational skills and insider knowledge that would make legitimate businesses jealous.
18. Warehouse Inventory Manipulation
An inside job where warehouse employees manipulated inventory systems to create “ghost inventory” for personal profit. Workers marked high-value items as damaged or returned while actually shipping them to their own addresses using fake shipping labels.
The scheme generated $720,000 in stolen inventory over 14 months before getting caught through routine audits. The manipulation was sophisticated enough to keep system records looking accurate while physically diverting merchandise.
The insider knowledge required made this type of fraud particularly hard to catch through automated systems. When your own employees are the criminals, traditional security measures don’t work.
| Supply Chain Weakness | Risk Level | How to Catch It | Prevention Cost |
|---|---|---|---|
| Package Theft | High | GPS Tracking | $2-5 per package |
| Warehouse Manipulation | Medium | Regular Audits | $50-200 per audit |
| Address Fraud | Medium | Address Verification | $0.50-1 per order |
| Customs Fraud | Low | Documentation Review | $100-500 per shipment |
19. Shipping Address Fraud
Fraudsters used vacant properties and mail forwarding services to create networks of fake shipping addresses for fraudulent purchases, making it nearly impossible to track them down or recover stolen goods. The operation included 400 fraudulent addresses used for 2,800 unauthorized purchases totaling $340,000.
The criminals carefully selected addresses that looked legitimate but allowed them to intercept packages without detection. They used mail forwarding services and temporary rental properties to create a web that was nearly impossible for law enforcement to untangle.
The distributed nature of the addresses made it challenging for merchants to spot patterns until significant losses had piled up.
20. Cross-Border Customs Fraud
An international fraud ring manipulated customs declarations and shipping documentation to avoid duties and taxes while importing counterfeit goods for e-commerce resale. The operation avoided $2.4 million in customs duties while generating $5.1 million in counterfeit goods sales.
The criminals exploited differences in international trade regulations and the fact that customs enforcement varies wildly between countries. They used sophisticated documentation fraud to lie about product values and classifications.
The cross-border nature made investigation and prosecution particularly challenging because of jurisdictional nightmares – nobody wanted to take responsibility for tracking down criminals operating across multiple countries.
Technology and Platform Exploitation Cases
Technology-based fraud represents the most sophisticated attacks, requiring serious technical skills to exploit vulnerabilities in APIs, mobile apps, and platform systems. These attacks often result in massive data breaches that enable tons of downstream fraud.
21. API Exploitation for Data Harvesting
An advanced threat group exploited vulnerabilities in e-commerce platform APIs to harvest customer data and payment information for large-scale fraud operations. They identified and exploited rate limiting weaknesses in REST APIs, used credential stuffing to access admin accounts, and extracted entire customer databases.
The scope was absolutely massive – 2.3 million customer records compromised across 40 e-commerce websites. The criminals sold this data on dark web marketplaces for other fraud campaigns, creating a multiplier effect that amplified the damage.
Direct platform losses hit $890,000, but the estimated downstream fraud using stolen data exceeded $12 million. These API vulnerabilities highlight why you need comprehensive security audits that examine both technical infrastructure and data protection measures.
22. Mobile App Reverse Engineering Fraud
Cybercriminals reverse-engineered popular shopping mobile apps to identify and exploit authentication weaknesses and payment processing vulnerabilities. They created modified app versions that bypassed payment verification while appearing to process transactions normally.
The technical sophistication required serious expertise in mobile application security and payment processing systems. The modified apps were distributed through unofficial channels and used to complete 15,000 fraudulent transactions worth $1.8 million.
Detection required sophisticated anomaly analysis to identify the unusual transaction patterns generated by the hacked applications.
23. Loyalty Program Points Manipulation
Fraudsters exploited weaknesses in loyalty program systems to artificially inflate point balances and convert rewards into cash. They identified race conditions in point allocation systems, used automated scripts to trigger multiple point awards for single actions, and created fake referral networks.
The technical approach required understanding system timing vulnerabilities and automated scripting capabilities. The operation generated $1.2 million in fraudulent rewards redemption across 25,000 compromised accounts.
The criminals converted inflated points to gift cards and merchandise, effectively turning system bugs into cold hard cash.
Social Engineering and Phishing Cases
Social engineering attacks exploit human psychology rather than technical vulnerabilities, and honestly, they’re often more effective than sophisticated technical attacks because they target the one security flaw you can’t patch – human nature under pressure.
24. Customer Service Social Engineering
A sophisticated social engineering campaign targeted e-commerce customer service representatives to gain unauthorized access to customer accounts and process fraudulent transactions. The criminals did their homework, researching customer service protocols through job postings and employee social media profiles.
They’d call support centers pretending to be customers with detailed personal information, use emotional manipulation and fake urgency to bypass security procedures, and convince representatives to override account security measures. The operation resulted in $560,000 in unauthorized transactions across 1,200 compromised accounts.
Here’s a real example: a fraudster calls customer service claiming to be “Sarah Johnson” who’s “locked out of her account while traveling for a family emergency.” They provide Sarah’s real address, phone number, and recent purchase history (stolen from a data breach). The stressed representative, wanting to help during an “emergency,” bypasses the usual security questions and resets the account password. Boom – the fraudster has complete access and makes $3,400 in unauthorized purchases.
The success rate was high because the criminals exploited inadequate security awareness training and unclear procedures for handling unusual requests.
25. Phishing-as-a-Service E-Commerce Targeting
A criminal organization operated a “Phishing-as-a-Service” platform specifically designed to target e-commerce customers with sophisticated, branded phishing campaigns. They provided turnkey phishing kits that perfectly mimicked popular e-commerce brands, offered hosting services on compromised websites, and included automated credential harvesting tools.
The service had 150 criminal subscribers who sent 50,000 phishing emails weekly with a 12% average success rate in credential harvesting. The operation generated $2.8 million in fraudulent purchases using harvested credentials.
The technical sophistication included machine learning to optimize phishing email content and bypass spam filters. It’s like criminals adopted the same business model as legitimate email marketing platforms, showing how professional these operations have become.
Key Analysis and Prevention Strategies
After going through all 25 cases, some clear patterns emerge in terms of financial impact, how long it takes to catch these scams, technical sophistication levels, and what actually works to prevent them. The goal is helping you figure out where to spend your security budget for maximum protection.
Financial Impact Assessment
The biggest money losers reveal important patterns. Phantom merchant schemes ($4.2M) show how professional presentation can massively scale fraud, while cross-border customs fraud ($5.1M in sales) demonstrates how criminals exploit regulatory gaps. Synthetic identity payment fraud ($2.3M) illustrates how patient, long-term criminal investment pays off big.
But here’s some good news – the most cost-effective prevention opportunities exist with simpler fraud types. Card testing attacks could be stopped 90% of the time with basic rate limiting, package theft risks drop dramatically with GPS tracking and delivery confirmation, and better return verification processes offer huge ROI against refund fraud.
Detection Timeline Patterns
Detection speed varies dramatically depending on the fraud type. Card testing attacks, API exploitation, and customer service social engineering can be caught within hours to days using automated systems, network monitoring tools, and call recording analysis.
The slowest detection cases are the most concerning. Child identity theft often stays hidden until credit applications years later, synthetic identity fraud requires sophisticated behavioral analysis, and warehouse inventory manipulation depends entirely on how often you audit.
| Prevention Strategy | Setup Cost | Success Rate | Payback Time |
|---|---|---|---|
| Rate Limiting | $500-2,000 | 90% for card testing | Right away |
| Multi-Factor Authentication | $2-10 per user | 85% for account takeover | 30 days |
| Address Verification | $0.50-1 per order | 70% for shipping fraud | 60 days |
| Behavioral Analysis | $10,000-50,000 | 75% for synthetic identity | 6 months |
| Employee Training | $200-500 per employee | 60% for social engineering | 90 days |
Technical Sophistication Breakdown
Low sophistication fraud (accessible to most criminals) includes social media identity harvesting, basic refund fraud, and simple shipping address fraud. These represent the highest volume threats that most businesses encounter regularly.
High sophistication fraud requires advanced technical skills but can cause massive damage. API exploitation, reverse engineering, synthetic identity creation networks, and advanced phishing-as-a-service operations represent the cutting edge of criminal capability.
Prevention Strategy Recommendations
High preventability cases should be your first priority. Rate limiting, CAPTCHA, velocity checks, multi-factor authentication, device fingerprinting, and enhanced return verification are readily available solutions with proven track records.
Medium preventability cases require investment in advanced solutions. Machine learning behavioral analysis, consortium data sharing, GPS tracking, delivery confirmation, supply chain security, advanced authentication, and risk scoring systems offer strong protection but need significant investment.
Low preventability cases are the toughest nuts to crack. Social engineering attacks need extensive human training and cultural change, insider fraud requires comprehensive background checks and ongoing monitoring, and advanced persistent threats demand enterprise-grade security infrastructure.
Look, I get it – nobody wants another text message every time they log in, and security measures can hurt conversion rates. But implementing these prevention strategies requires careful ROI analysis to ensure security investments align with business objectives and expected fraud losses.
How The Marketing Agency Can Help
The Marketing Agency’s data-driven approach to digital marketing can be applied to fraud prevention challenges, helping e-commerce businesses turn security investments into competitive advantages while maintaining customer trust and conversion rates.
Your fraud prevention efforts shouldn’t kill your marketing performance – they should actually enhance it. I’ve seen too many businesses implement security measures that hurt conversion rates or create so much customer friction that sales go to competitors instead.
Our data-driven approach helps you implement fraud prevention that actually improves customer experience. We use advanced analytics to identify legitimate customer patterns versus fraudulent behavior, reducing false positive rates that damage conversion rates. This means your security measures protect your business without hurting your bottom line.
Our team leverages advanced analytics to help you understand customer behavior patterns and implement security measures that protect against fraud while maintaining optimal user experience.
When fraud incidents do happen, we provide crisis communication strategies backed by performance data. Our reputation management services help you maintain customer trust during security incidents while our SEO and content marketing strategies rebuild brand credibility after fraud-related negative publicity.
We also help you turn security investments into competitive advantages. Our content marketing team creates educational content about e-commerce security best practices, positioning you as a trustworthy industry leader while improving organic search visibility for security-related keywords.
Our conversion optimization expertise ensures fraud prevention measures don’t negatively impact user experience or sales performance. We apply performance marketing principles to help you calculate ROI for various fraud prevention tools, ensuring security spending aligns with business growth objectives.
Through our comprehensive service offering – from PPC campaigns ($750-$5,000/month) educating customers about security best practices to email marketing sequences ($1,200-$10,000/month) building customer loyalty through security education – we help you transform fraud prevention from a cost center into a competitive advantage.
Understanding the complete scope of these fraud case study examples helps inform our approach to developing content marketing strategies that build customer trust while educating your audience about security best practices.
Ready to turn your security investments into marketing advantages? Contact us to discuss how our data-driven approach can help you prevent fraud while growing your business.
Final Thoughts
These 25 case studies reveal a pretty sobering reality about e-commerce fraud – it’s getting more common, smarter, and frankly more terrifying. The criminals behind these schemes aren’t just opportunistic amateurs throwing stuff at the wall to see what sticks. They’re sophisticated operators who invest months or years building credible operations before they strike.
What really gets to me is how these fraudsters exploit the very things that make e-commerce work – our trust systems, generous return policies, streamlined checkout processes. Every convenience we create for legitimate customers becomes a potential vulnerability for criminals to exploit.
The financial numbers are staggering, but the real cost goes way beyond immediate losses. When customers lose trust in online shopping, when legitimate businesses can’t compete with fake review manipulation, when elderly victims become afraid to use technology – that’s when fraud truly wins.
Writing about these cases honestly made me want to go check my own accounts three times. The scariest part isn’t just the money – it’s how these scams make you question every single online transaction. Should I really trust this website? Is this email legit? It’s absolutely exhausting.
However, I’m encouraged by the prevention opportunities these cases reveal. Many of the most damaging fraud types are actually preventable with existing technology and proper implementation. This is one of those “why isn’t everyone doing this already?” situations. The key is balancing security with customer experience, which requires both technical expertise and marketing insight.
Your fraud prevention strategy shouldn’t be an afterthought tacked on after everything else is built. It should be integrated into your customer experience and marketing strategy from day one. The businesses that’ll thrive are those that can provide both security and convenience, turning fraud prevention into a competitive advantage rather than a necessary evil.
If this doesn’t make you want to review your security measures right now, I don’t know what will.